The Security Tools protect assets at operational level en block unfamiliar traffic. Connection to the AX-CONTROL Platform creates full control.
International cyber intelligence, frameworks and guidelines are integrated into the Platform to protect against the latest known vulnerabilities.

Data integrity in combination with putting the data in context at a specific operational location is combined with fully automated hardening and compliance. This creates real-time auditable configuration integrity and change control and the ability not only to flag, but also to block any unfamiliar traffic that disrupts operations. The Platform delivers visibility and in-depth insight in emerging events to fully control the integrity of data and configuration.
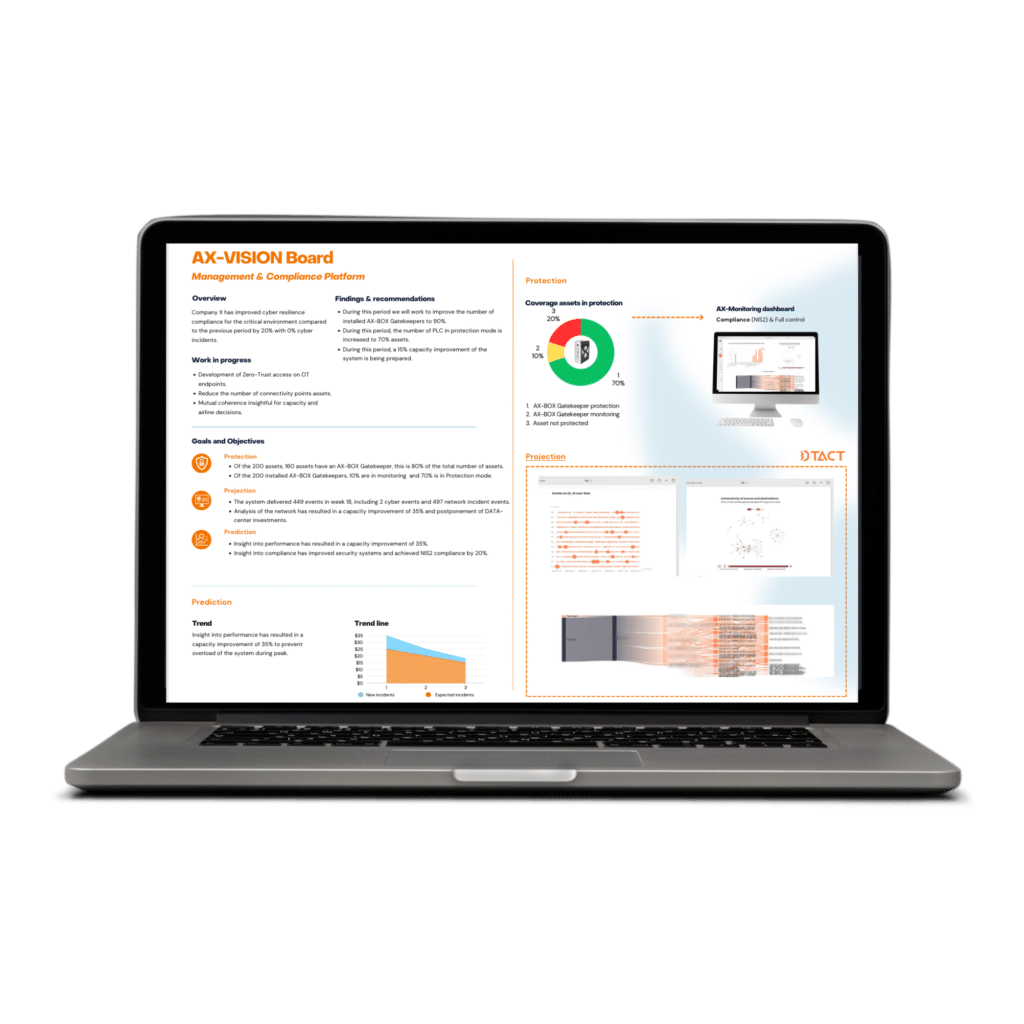
The AX-Vision Board is powerful as a risk management tool, allowing organizations to achieve an advanced level of control and insight over their OT infrastructure. Relying on automated analysis and alerts, you can respond more quickly to potential threats and ensure operational continuity. This contributes to a vast improvement in security and enables organizations to remain resilient and agile amid an ever-evolving threat landscape.
When developing the AX-Vision Board, we worked closely with DTACT, a Dutch company specialized in visualizing and exploring big data flows. Together we unlocked the linked sources and correlated the data for use on the AX-Vision Board. This allows the AX-Vision Board to provide insight at every level within an organization.

The AX-BOX Gatekeeper is built for mission critical systems and is able to execute “Zero-Trust” access management to legacy end-point controllers in the field. It runs a unique Artificial Intelligence detection program to detect anomalies, such as reconnaissance, in communication at a specific location. In addition, it has the possibility to set rules for smart configuration management, based blacklisting, controlled service support or the essence of a paired systems.
This tool is used to achieve unmatched easy hardening, trough fully automated STIG and CIS compliance.
The AX-CONTROL keeper is a game changer for accreditation readiness and ongoing robustness. This is smart cybersecurity through automation.


Dutch product, made by technical people with decades of experience in technology and different operational environments.



